
More than 6 years ago (!) I published a tutorial on how to set up an IPsec VPN tunnel between a FortiGate firewall and a Cisco ASA. As time flies by, ASA is now able to terminate route-based VPN tunnels (which is great!), we have IKEv2 running everywhere and enhanced security proposals. Hence, it’s time for an update:
My Setup
This is my setup for this tutorial: (Yes, public IPv4 addresses behind the Forti.)
I am using a Fortinet FortiWiFi FWF-61E with FortiOS v6.2.5 build1142 (GA) and a Cisco ASA 5515 with version 9.12(3)12 and ASDM 7.14(1). These are the VPN parameters:
- Route-based VPN, that is: numbered tunnel interface and real route entries for the network(s) to the other side. But no proxy-IDs aka traffic selection aka crypto map. Thank goodness for that.
- The tunnel interface on the Forti is added during the VPN setup automatically. However, you have to set the IP address on the tunnel interface manually after that. The static route on the ASA needs an IP address as the gateway.
- IKEv2 (no distinction anymore between main or aggressive mode as with IKEv1)
- PSK: 30 chars alphanumeric, generated with a password generator! (ref)
- IKE crypto/policies:
- Diffie-Hellman group 21
- AES-256-GCM
- SHA-512 (you could use SHA-256 if you like)
- 8 hours
- IPsec crypto/proposals/transform sets:
- AES-256-GCM
- SHA-512 (again, you can use SHA-256 as well)
- Diffie-Hellman group 21
- 1 hour
- No NAT between the internal networks (of course not ;))!
FortiGate
You can do the configuration through the GUI:

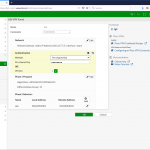

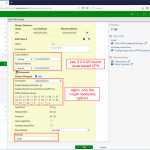
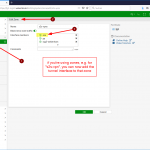



or through the CLI: (incl. the zone commands <- can be omitted if you aren’t using zones)
config system interface
edit "asa"
set vdom "root"
set ip 10.1.37.1 255.255.255.255
set allowaccess ping
set type tunnel
set remote-ip 10.1.37.2 255.255.255.252
set interface "wan1"
next
end
config system zone
edit "s2s-vpns"
set interface "asa"
next
end
config vpn ipsec phase1-interface
edit "asa"
set interface "wan1"
set ike-version 2
set keylife 28800
set peertype any
set net-device enable
set proposal aes256gcm-prfsha512
set dhgrp 21
set nattraversal disable
set remote-gw 185.23.77.7
set psksecret ThisIsThePreSharedKey
next
end
config vpn ipsec phase2-interface
edit "asa"
set phase1name "asa"
set proposal aes256gcm
set dhgrp 21
set keylifeseconds 3600
next
end
config router static
edit 5
set dst 172.16.37.0 255.255.255.0
set device "asa"
next
end
Cisco ASA
Same on the ASA, either via the “GUI”:
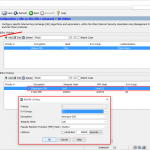
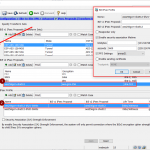



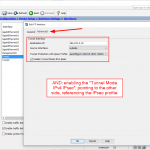


or via classical CLI commands: (The ACL is omitted.)
interface Tunnel1 nameif fg2 ip address 10.1.37.2 255.255.255.252 tunnel source interface outside tunnel destination 194.247.4.10 tunnel mode ipsec ipv4 tunnel protection ipsec profile aes256gcm-sha512-dh21-3600s ! route fg2 194.247.5.0 255.255.255.224 10.1.37.1 1 ! crypto ipsec ikev2 ipsec-proposal aes256gcm-sha512 protocol esp encryption aes-gcm-256 protocol esp integrity sha-512 crypto ipsec profile aes256gcm-sha512-dh21-3600s set ikev2 ipsec-proposal aes256gcm-sha512 set pfs group21 set security-association lifetime seconds 3600 crypto ikev2 policy 1 encryption aes-gcm-256 integrity null group 21 prf sha512 lifetime seconds 28800 ! group-policy 194.247.4.10 internal group-policy 194.247.4.10 attributes vpn-tunnel-protocol ikev2 tunnel-group 194.247.4.10 type ipsec-l2l tunnel-group 194.247.4.10 general-attributes default-group-policy 194.247.4.10 tunnel-group 194.247.4.10 ipsec-attributes ikev2 remote-authentication pre-shared-key ThisIsThePreSharedKey ikev2 local-authentication pre-shared-key ThisIsThePreSharedKey
Monitoring
Some screenshots from the FortiGate:


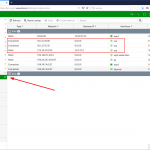
as well as CLI outputs:
fg2 # get vpn ike gateway asa
vd: root/0
name: asa
version: 2
interface: wan1 6
addr: 194.247.4.10:500 -> 185.23.77.7:500
created: 3158587s ago
IKE SA created: 1/111 established: 1/111 time: 0/3/100 ms
IPsec SA created: 1/973 established: 1/973 time: 0/0/100 ms
id/spi: 2040 7be16624b6a980a3/b107958ab150a4fb
direction: initiator
status: established 23585-23585s ago = 10ms
proposal: unknown-256-unknown
SK_ei: c301af190feb89e7-e89076489227f77e-73a80ecd3692c0c7-925c73a84a30c063-618eb9af
SK_er: 5362b4bc6103b45f-776a3e817a61026f-75b7cd0220fb8d70-05f32a71240799e6-f1441bb6
SK_ai:
SK_ar:
lifetime/rekey: 28800/4914
DPD sent/recv: 00000000/00000000
fg2 #
fg2 #
fg2 # get vpn ipsec tunnel name asa
gateway
name: 'asa'
type: route-based
local-gateway: 194.247.4.10:0 (static)
remote-gateway: 185.23.77.7:0 (static)
mode: ike-v2
interface: 'wan1' (6)
rx packets: 110976 bytes: 145943836 errors: 0
tx packets: 64092 bytes: 3004962 errors: 0
dpd: on-demand/negotiated idle: 20000ms retry: 3 count: 0
selectors
name: 'asa'
auto-negotiate: disable
mode: tunnel
src: 0:0.0.0.0/0.0.0.0:0
dst: 0:0.0.0.0/0.0.0.0:0
SA
lifetime/rekey: 3600/2171
mtu: 1446
tx-esp-seq: 27
replay: enabled
qat: 0
inbound
spi: 15ad154f
enc: aes-gc e1831416107c6ca5c1d6da624269ba4e21b7d45c95d5a16da8c0f9200b598ebbab76f5b9
auth: null
outbound
spi: 9573f1de
enc: aes-gc 3d6e5ab8c1ac1de02a230095d76778dd5b88aeeff7dfae8b25df26c265bdec56710d040e
auth: null
NPU acceleration: none
fg2 #
fg2 #
fg2 # diagnose vpn tunnel list name asa
list ipsec tunnel by names in vd 0
------------------------------------------------------
name=asa ver=2 serial=3 194.247.4.10:0->185.23.77.7:0 dst_mtu=1500
bound_if=6 lgwy=static/1 tun=intf/0 mode=auto/1 encap=none/536 options[0218]=npu create_dev frag-rfc accept_traffic=1 overlay_id=0
proxyid_num=1 child_num=0 refcnt=14 ilast=12 olast=12 ad=/0
stat: rxp=110977 txp=64094 rxb=145943972 txb=3005118
dpd: mode=on-demand on=1 idle=20000ms retry=3 count=0 seqno=440
natt: mode=none draft=0 interval=0 remote_port=0
proxyid=asa proto=0 sa=1 ref=3 serial=2
src: 0:0.0.0.0/0.0.0.0:0
dst: 0:0.0.0.0/0.0.0.0:0
SA: ref=3 options=10226 type=00 soft=0 mtu=1446 expire=2114/0B replaywin=1024
seqno=29 esn=0 replaywin_lastseq=00000014 itn=0 qat=0 hash_search_len=1
life: type=01 bytes=0/0 timeout=3298/3600
dec: spi=15ad154f esp=aes-gcm key=36 e1831416107c6ca5c1d6da624269ba4e21b7d45c95d5a16da8c0f9200b598ebbab76f5b9
ah=null key=0
enc: spi=9573f1de esp=aes-gcm key=36 3d6e5ab8c1ac1de02a230095d76778dd5b88aeeff7dfae8b25df26c265bdec56710d040e
ah=null key=0
dec:pkts/bytes=20/1600, enc:pkts/bytes=40/5360
npu_flag=20 npu_rgwy=185.23.77.7 npu_lgwy=194.247.4.10 npu_selid=5 dec_npuid=0 enc_npuid=0
fg2 #
fg2 #
fg2 # get router info routing-table all
Routing table for VRF=0
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
S* 0.0.0.0/0 [10/0] via 194.247.4.1, wan1
C 10.1.37.0/30 is directly connected, asa
C 10.1.37.1/32 is directly connected, asa
S 172.16.37.0/24 [10/0] via 10.1.37.2, asa
S 192.168.11.0/24 [10/0] is directly connected, ssg5-weberhom
S 193.24.227.224/27 [10/0] is directly connected, pa
C 194.247.4.0/27 is directly connected, wan1
C 194.247.5.0/27 is directly connected, internal
fg2 #And some screenshots from the ASA: (the third one showing the logs after a manual “logout”)


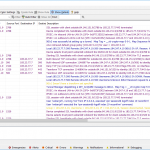
as well as CLI outputs:
asa# show crypto ikev2 sa detail
IKEv2 SAs:
Session-id:16, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
1219040189 185.23.77.7/500 194.247.4.10/500 READY INITIATOR
Encr: AES-GCM, keysize: 256, Hash: N/A, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 28800/298 sec
Session-id: 16
Status Description: Negotiation done
Local spi: E82116F37CF38D12 Remote spi: 3D48FE4CB448BA6B
Local id: 185.23.77.7
Remote id: 194.247.4.10
Local req mess id: 26 Remote req mess id: 0
Local next mess id: 26 Remote next mess id: 0
Local req queued: 26 Remote req queued: 0
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is not detected
IKEv2 Fragmentation Configured MTU: 576 bytes, Overhead: 28 bytes, Effective MTU: 548 bytes
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 0.0.0.0/0 - 255.255.255.255/65535
ESP spi in/out: 0x5f713ed2/0x15ad1552
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-GCM, keysize: 256, esp_hmac: N/A
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Parent SA Extended Status:
Delete in progress: FALSE
Marked for delete: FALSE
asa#
asa#
asa# show crypto ipsec sa peer 194.247.4.10 detail
peer address: 194.247.4.10
Crypto map tag: __vti-crypto-map-5-0-1, seq num: 65280, local addr: 185.23.77.7
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 194.247.4.10
#pkts encaps: 29, #pkts encrypt: 29, #pkts digest: 29
#pkts decaps: 45, #pkts decrypt: 45, #pkts verify: 45
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 29, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#pkts no sa (send): 0, #pkts invalid sa (rcv): 0
#pkts encaps failed (send): 0, #pkts decaps failed (rcv): 0
#pkts invalid prot (rcv): 0, #pkts verify failed: 0
#pkts invalid identity (rcv): 0, #pkts invalid len (rcv): 4009213712
#pkts invalid pad (rcv): 0,
#pkts invalid ip version (send): 0, #pkts invalid ip version (rcv): 0
#pkts invalid len (send): 0, #pkts invalid len (rcv): 0
#pkts invalid ctx (send): 0, #pkts invalid ctx (rcv): 0
#pkts invalid ifc (send): 0, #pkts invalid ifc (rcv): 0
#pkts failed (send): 0, #pkts failed (rcv): 0
#pkts replay rollover (send): 0, #pkts replay rollover (rcv): 0
#pkts replay failed (rcv): 0
#pkts min mtu frag failed (send): 0, #pkts bad frag offset (rcv): 0
#pkts internal err (send): 0, #pkts internal err (rcv): 0
local crypto endpt.: 185.23.77.7/500, remote crypto endpt.: 194.247.4.10/500
path mtu 1500, ipsec overhead 55(36), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 15AD1552
current inbound spi : 5F713ED2
inbound esp sas:
spi: 0x5F713ED2 (1601257170)
SA State: active
transform: esp-aes-gcm-256 esp-null-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 21, IKEv2, VTI, }
slot: 0, conn_id: 51, crypto-map: __vti-crypto-map-5-0-1
sa timing: remaining key lifetime (kB/sec): (3962873/3231)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0xAAAAAAAA 0xAAAAB8AA
outbound esp sas:
spi: 0x15AD1552 (363664722)
SA State: active
transform: esp-aes-gcm-256 esp-null-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 21, IKEv2, VTI, }
slot: 0, conn_id: 51, crypto-map: __vti-crypto-map-5-0-1
sa timing: remaining key lifetime (kB/sec): (4193275/3231)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
asa#
asa#
asa# show route static
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 185.23.77.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 185.23.77.1, outside
S 194.247.5.0 255.255.255.224 [1/0] via 10.1.37.1, fg2
asa#
PS: Sorry for being legacy IP only this time. ;(
Photo by Casey Horner on Unsplash.
