For some reason, I came across a blog post by Gian Paolo called Small servers. This reminded me of some fairly old network protocols (that no one uses as far as I know) that are not in my Ultimate PCAP yet. Hence I took some minutes, captured them, and took some Wireshark screenshots. They are: echo, discard, daytime, chargen, and time. Mostly via TCP and UDP, and, as you would have expected, IPv6 and legacy IP.
I’m aware that this is not of interest to most of you. :) But for the sake of completeness, and because I love adding new protocols to the Ultimate PCAP, I added them though.
I used an old Cisco 2811 router with IOS version 15.1(4)M12a for this:
service udp-small-servers service tcp-small-servers
The registered transport protocol port numbers and the transport layer protocols implemented on Cisco routers are:
| Port | Name | TCP | UDP |
|---|---|---|---|
| 7 | Echo | ✅ | ✅ |
| 9 | Discard | ✅ | ✅ |
| 13 | Daytime | ✅ | ❌ |
| 19 | Chargen | ✅ | ✅ |
| 37 | Time | ❌ | ❌ |
For the daytime to work with UDP, I queried my Meinberg LANTIME M200 at ntp3.weberlab.de (AAAA) and ntp3-legacy-ip.weberlab.de (A) respectively. Furthermore, I also queried the “time” protocol, port number 37, against the Meinberg since it is not implemented by Ciscos small-servers.
Some Nmap scans, just for reference:
weberjoh@h2877111:~$ nmap -6 router1.weberlab.de Starting Nmap 7.80 ( https://nmap.org ) at 2022-10-20 13:08 CEST Nmap scan report for router1.weberlab.de (2001:470:1f0a:319::2) Host is up (0.033s latency). Other addresses for router1.weberlab.de (not scanned): 37.24.166.89 rDNS record for 2001:470:1f0a:319::2: tunnel643592-pt.tunnel.tserv6.fra1.ipv6.he.net Not shown: 996 closed ports PORT STATE SERVICE 7/tcp open echo 9/tcp open discard 13/tcp open daytime 19/tcp open chargen Nmap done: 1 IP address (1 host up) scanned in 8.79 seconds weberjoh@h2877111:~$ weberjoh@h2877111:~$ weberjoh@h2877111:~$ nmap router1.weberlab.de Starting Nmap 7.80 ( https://nmap.org ) at 2022-10-20 13:07 CEST Nmap scan report for router1.weberlab.de (37.24.166.89) Host is up (0.047s latency). Other addresses for router1.weberlab.de (not scanned): 2001:470:1f0a:319::2 rDNS record for 37.24.166.89: ip-037-024-166-089.um08.pools.vodafone-ip.de Not shown: 996 closed ports PORT STATE SERVICE 7/tcp open echo 9/tcp open discard 13/tcp open daytime 19/tcp open chargen Nmap done: 1 IP address (1 host up) scanned in 5.82 seconds weberjoh@h2877111:~$ weberjoh@h2877111:~$ weberjoh@h2877111:~$ sudo nmap -6 -sU -p 7,9,13,19 router1.weberlab.de Starting Nmap 7.80 ( https://nmap.org ) at 2022-10-20 13:19 CEST Nmap scan report for router1.weberlab.de (2001:470:1f0a:319::2) Host is up (0.10s latency). Other addresses for router1.weberlab.de (not scanned): 37.24.166.89 rDNS record for 2001:470:1f0a:319::2: tunnel643592-pt.tunnel.tserv6.fra1.ipv6.he.net PORT STATE SERVICE 7/udp open echo 9/udp closed discard 13/udp closed daytime 19/udp closed chargen Nmap done: 1 IP address (1 host up) scanned in 2.15 seconds weberjoh@h2877111:~$ weberjoh@h2877111:~$ weberjoh@h2877111:~$ sudo nmap -sU -p 7,9,13,19 router1.weberlab.de Starting Nmap 7.80 ( https://nmap.org ) at 2022-10-20 13:18 CEST Nmap scan report for router1.weberlab.de (37.24.166.89) Host is up (0.030s latency). Other addresses for router1.weberlab.de (not scanned): 2001:470:1f0a:319::2 rDNS record for 37.24.166.89: ip-037-024-166-089.um08.pools.vodafone-ip.de PORT STATE SERVICE 7/udp open echo 9/udp open|filtered discard 13/udp closed daytime 19/udp open|filtered chargen Nmap done: 1 IP address (1 host up) scanned in 10.70 seconds weberjoh@h2877111:~$ weberjoh@h2877111:~$ weberjoh@h2877111:~$ sudo nmap -6 -sU -p 13 ntp3.weberlab.de Starting Nmap 7.80 ( https://nmap.org ) at 2022-11-18 08:55 CET Nmap scan report for ntp3.weberlab.de (2001:470:1f0b:16b0::dcfb:123) Host is up (0.022s latency). PORT STATE SERVICE 13/udp open daytime Nmap done: 1 IP address (1 host up) scanned in 4.21 seconds weberjoh@h2877111:~$ pi@pi05-random:~ $ pi@pi05-random:~ $ sudo nmap -sU -p 13 ntp3-legacy-ip.weberlab.de Starting Nmap 7.40 ( https://nmap.org ) at 2022-11-18 11:55 CET Nmap scan report for ntp3-legacy-ip.weberlab.de (194.247.5.12) Host is up (0.00048s latency). PORT STATE SERVICE 13/udp open daytime MAC Address: 00:13:95:24:34:04 (congatec AG) Nmap done: 1 IP address (1 host up) scanned in 1.33 seconds
Calling Them: Basically Telnet
To be honest, all of those protocols basically rely on mere TCP or UDP, just like HTTP or SMTP or all the other plaintext protocols out there. That is: telnet and netcat for these scenarios here. Now for all those 5 protocols, I did 4x calls each, namely TCP for IPv6 and legacy IP, as well as UDP for IPv6 and legacy IP. I referenced the protocols by either their name or their numerical number: (Reminder: Exiting telnet with ^] which is “Strg +” on a german keyboard.)
###echo #exiting telnet with "Strg +" and "quit" telnet router1.weberlab.de echo telnet -4 router1.weberlab.de echo netcat -u router1.weberlab.de 7 netcat -4 -u router1.weberlab.de 7 ###discard #exiting telnet with "Strg +" and "quit" telnet router1.weberlab.de discard telnet -4 router1.weberlab.de discard netcat -u router1.weberlab.de 9 netcat -4 -u router1.weberlab.de 9 ###daytime #exiting telnet with "Strg +" and "quit" telnet router1.weberlab.de daytime telnet -4 router1.weberlab.de daytime telnet ntp3.weberlab.de 13 telnet ntp3-legacy-ip.weberlab.de 13 #UDP needs an enter key to respond netcat -u ntp3.weberlab.de 13 netcat -u ntp3-legacy-ip.weberlab.de 13 ###chargen #exiting telnet with "Strg +" and "quit" telnet router1.weberlab.de chargen telnet -4 router1.weberlab.de chargen netcat -u router1.weberlab.de 19 netcat -4 -u router1.weberlab.de 19 ###time #exiting telnet with "Strg +" and quit telnet ntp3.weberlab.de time telnet ntp3-legacy-ip.weberlab.de time #UDP needs an enter key to respond netcat -u ntp3.weberlab.de 37 netcat -u ntp3-legacy-ip.weberlab.de 37
The complete story is this:
weberjoh@h2877111:~$ telnet router1.weberlab.de echo Trying 2001:470:1f0a:319::2... Connected to router1.weberlab.de. Escape character is '^]'. hello world hello world yup yup here we go here we go ^] telnet> quit Connection closed. weberjoh@h2877111:~$ telnet -4 router1.weberlab.de echo Trying 37.24.166.89... Connected to router1.weberlab.de. Escape character is '^]'. same here same here but with legacy IP ;D but with legacy IP ;D ^] telnet> quit Connection closed. weberjoh@h2877111:~$ netcat -u router1.weberlab.de 7 what about UDP what about UDP yeah yeah ^C weberjoh@h2877111:~$ netcat -4 -u router1.weberlab.de 7 as well as for legacy IP here as well as for legacy IP here ciao ciao ^C weberjoh@h2877111:~$ telnet router1.weberlab.de discard Trying 2001:470:1f0a:319::2... Connected to router1.weberlab.de. Escape character is '^]'. discarding everything ^] telnet> quit Connection closed. weberjoh@h2877111:~$ telnet -4 router1.weberlab.de discard Trying 37.24.166.89... Connected to router1.weberlab.de. Escape character is '^]'. foo bar ^] telnet> quit Connection closed. weberjoh@h2877111:~$ netcat -u router1.weberlab.de 9 was sollen wir trinken? weberjoh@h2877111:~$ netcat -4 -u router1.weberlab.de 9 sieben Tage lang was sollen wir trinken? so ein Durst! ^C weberjoh@h2877111:~$ telnet router1.weberlab.de daytime Trying 2001:470:1f0a:319::2... Connected to router1.weberlab.de. Escape character is '^]'. Friday, November 18, 2022 13:03:03-CET Connection closed by foreign host. weberjoh@h2877111:~$ telnet -4 router1.weberlab.de daytime Trying 37.24.166.89... Connected to router1.weberlab.de. Escape character is '^]'. Friday, November 18, 2022 13:03:12-CET Connection closed by foreign host. weberjoh@h2877111:~$ telnet ntp3.weberlab.de 13 Trying 2001:470:1f0b:16b0::dcfb:123... Connected to ntp3.weberlab.de. Escape character is '^]'. 18 NOV 2022 12:03:18 UTC Connection closed by foreign host. weberjoh@h2877111:~$ telnet ntp3-legacy-ip.weberlab.de 13 Trying 194.247.5.12... Connected to ntp3-legacy-ip.weberlab.de. Escape character is '^]'. 18 NOV 2022 12:03:21 UTC Connection closed by foreign host. weberjoh@h2877111:~$ netcat -u ntp3.weberlab.de 13 18 NOV 2022 12:03:26 UTC 18 NOV 2022 12:03:27 UTC 18 NOV 2022 12:03:29 UTC 18 NOV 2022 12:03:30 UTC 18 NOV 2022 12:03:30 UTC 18 NOV 2022 12:03:30 UTC 18 NOV 2022 12:03:30 UTC 18 NOV 2022 12:03:30 UTC ^C weberjoh@h2877111:~$ netcat -u ntp3-legacy-ip.weberlab.de 13 ^C weberjoh@h2877111:~$ telnet router1.weberlab.de chargen Trying 2001:470:1f0a:319::2... Connected to router1.weberlab.de. Escape character is '^]'. !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefg !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefgh "#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghi #$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghij $%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijk %&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijkl &'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklm '()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmn ()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmno )*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnop *+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopq +,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqr ,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrs -./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrst ./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstu ^] telnet> quit Connection closed. weberjoh@h2877111:~$ telnet -4 router1.weberlab.de chargen Trying 37.24.166.89... Connected to router1.weberlab.de. Escape character is '^]'. !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefg !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefgh "#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghi #$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghij $%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijk %&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijkl &'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklm '()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmn ()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmno )*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnop *+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopq +,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqr ,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrs -./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrst ./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstu /0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuv ^] telnet> quit Connection closed. weberjoh@h2877111:~$ netcat -u router1.weberlab.de 19 weberjoh@h2877111:~$ netcat -4 -u router1.weberlab.de 19 asdf ^C weberjoh@h2877111:~$ telnet ntp3.weberlab.de time Trying 2001:470:1f0b:16b0::dcfb:123... Connected to ntp3.weberlab.de. Escape character is '^]'. ▒!▒<Connection closed by foreign host. weberjoh@h2877111:~$ telnet ntp3-legacy-ip.weberlab.de time Trying 194.247.5.12... Connected to ntp3-legacy-ip.weberlab.de. Escape character is '^]'. ▒!▒@Connection closed by foreign host. weberjoh@h2877111:~$ netcat -u ntp3.weberlab.de 37 ▒!▒D ▒!▒E ▒!▒F^C weberjoh@h2877111:~$ netcat -u ntp3-legacy-ip.weberlab.de 37 ^C weberjoh@h2877111:~$
Note that the “time” protocol is the only one which does not display ASCII characters in the telnet session, but kind of junk. ;) This is due to its format: “The server then sends the time as a 32-bit unsigned integer in binary format and in network byte order, representing the number of seconds since 00:00 (midnight) 1 January, 1900 GMT.”
Under the Magnifying Glass: Wireshark
Let’s have a brief look at those protocols with Wireshark.
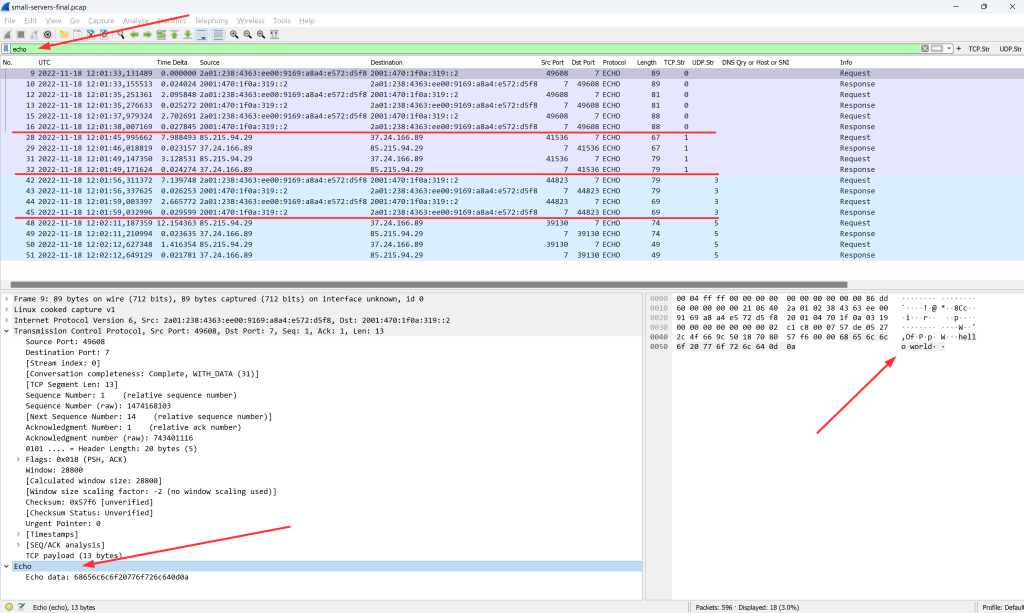
Echo
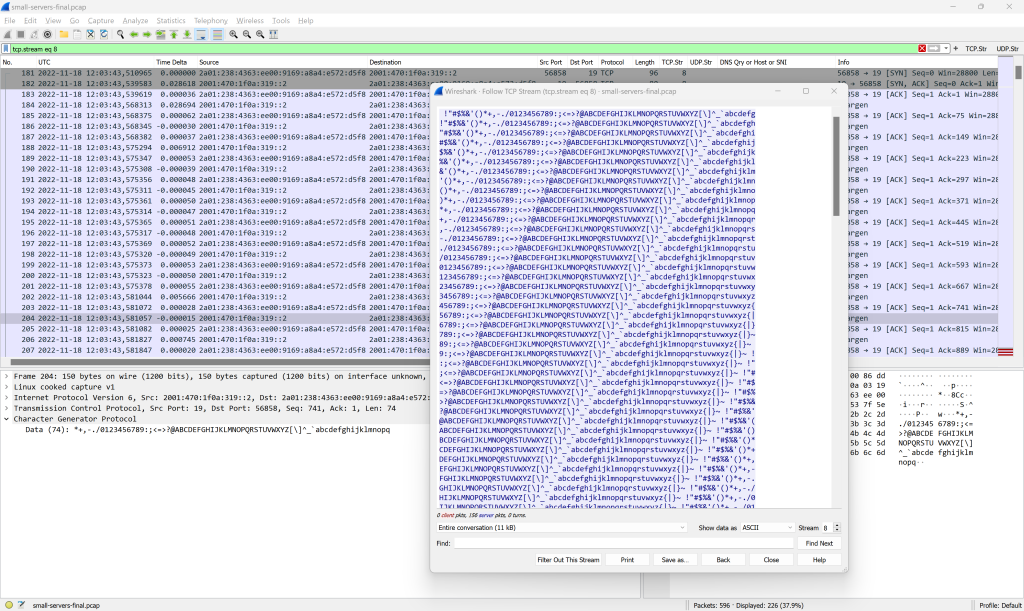
The Echo protocol simply sends back everything it has received. Specified in RFC 862. Fun fact: The whole RFC is only ONE PAGE!!!
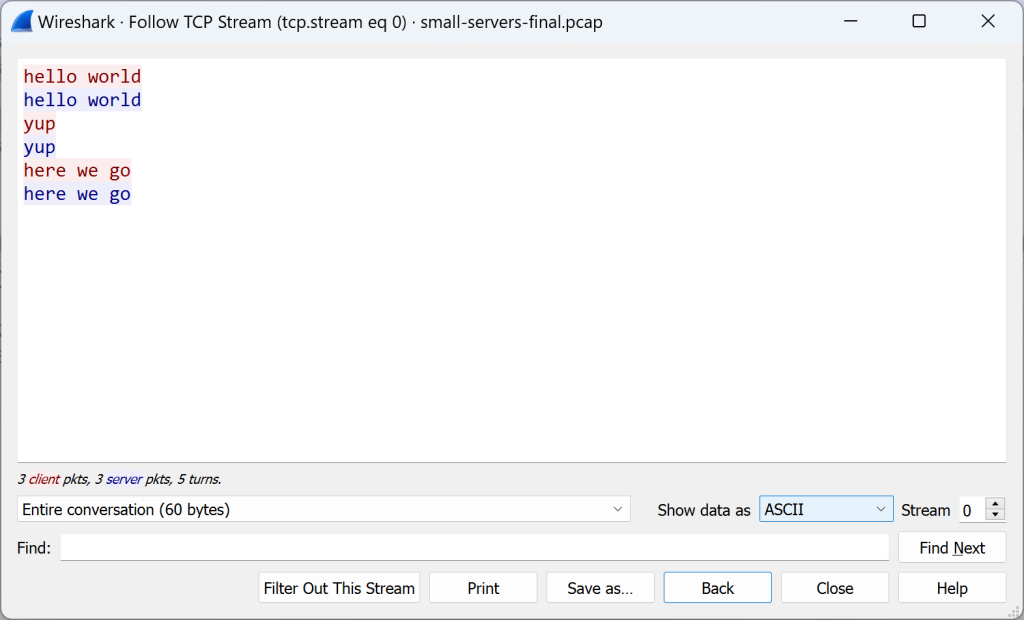
As you can see in the screenshot, I’ve done it via TCP and UDP, both for IPv6 and legacy IP. A good time to point to the “Follow TCP Stream” or “Follow UDP Stream” again:
Discard
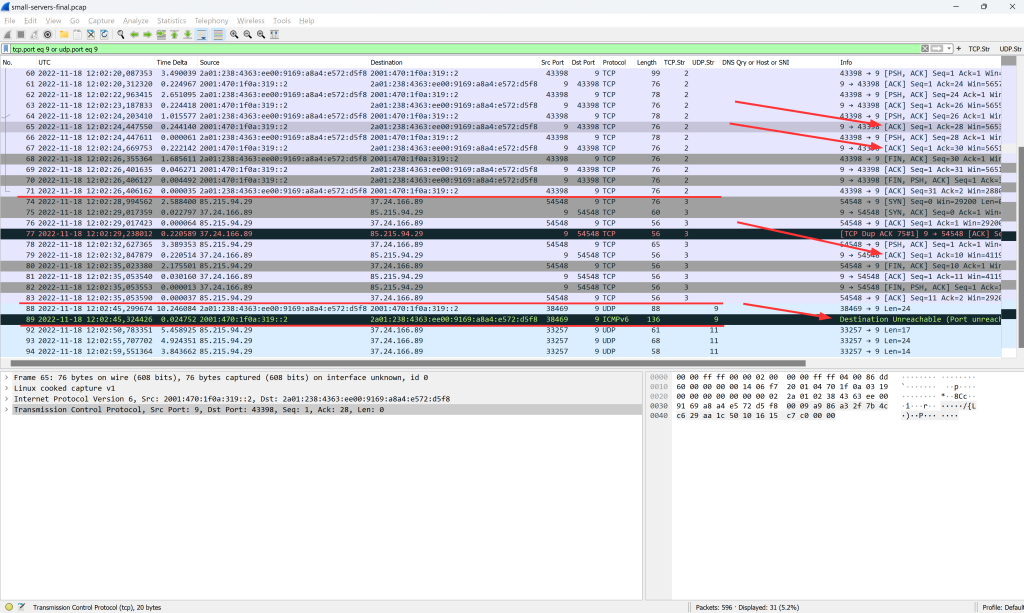
Uh, as of now (November 2022), Wireshark does not yet recognize the “Discard” protocol at port 9. I added a feature request here. Use this display filter to find it nevertheless: tcp.port eq 9 or udp.port eq 9
The Discard service, RFC 863, simply discards everything it has received. For TCP, everything is ACKed at least (no data is sent back, though), while for UDP you won’t see any packets from the server. However, seems like my router did not listen on the Discard port 9 for UDP on IPv6, since an ICMPv6 destination unreachable -> port unreachable came back:
Daytime
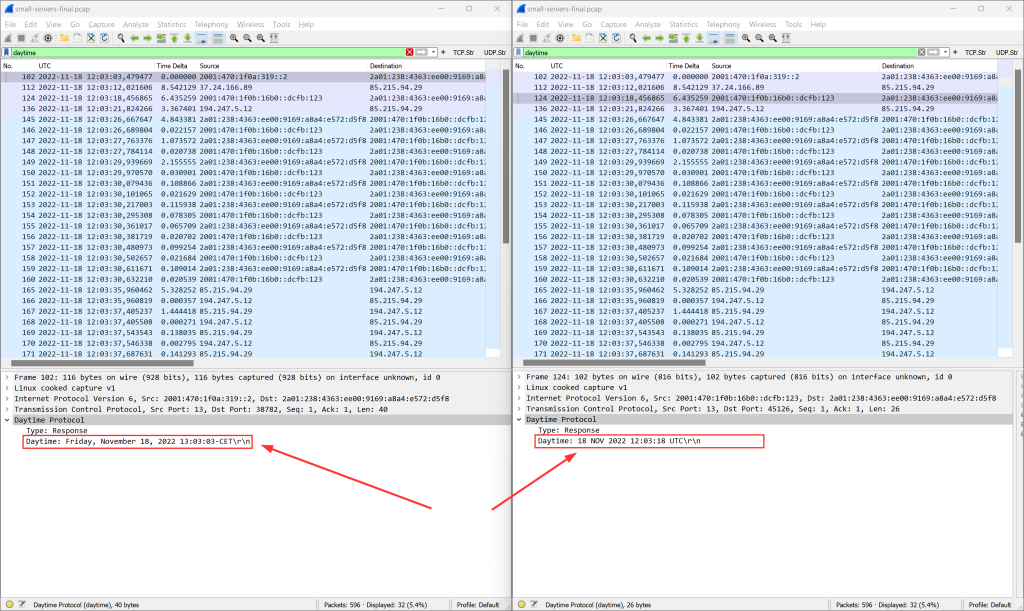
“A daytime service simply sends the current date and time as a character string without regard to the input”, RFC 867. Different implementations send different structures of pure ASCII letters:
Chargen
The Character Generator Protocol “simply sends data without regard to the input”, RFC 864. My Cisco router only replied by TCP though. Good example to “Follow TCP Stream” again:
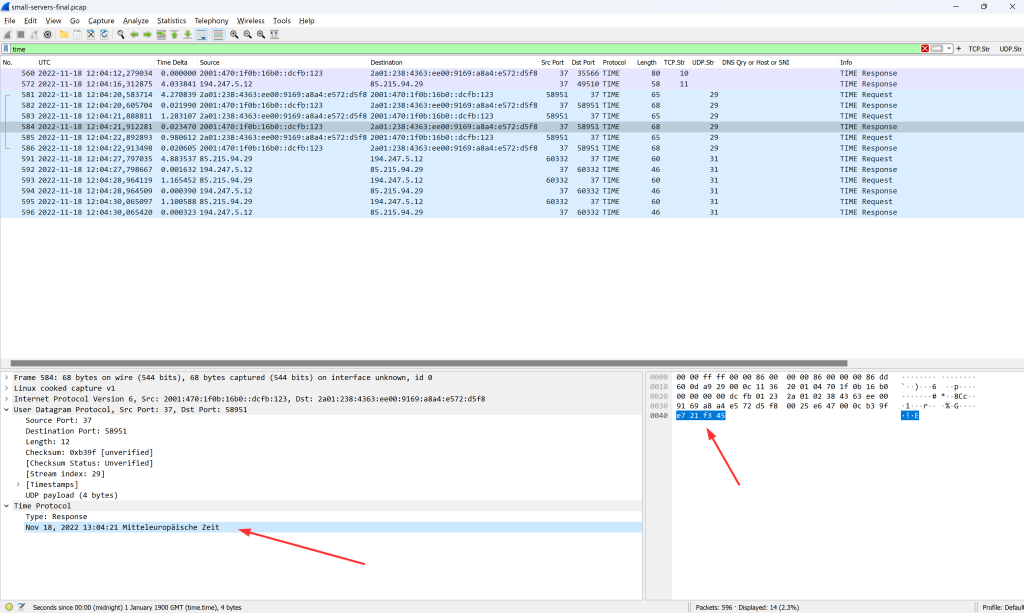
Time
Finally, the Time protocol on port 37, RFC 868, returns the number of seconds since 01.01.1900. Wireshark decodes it:
The End
And yes, at the very end, I disabled those small-servers again on the Cisco router:
no service udp-small-servers no service tcp-small-servers
Photo by Kris-Mikael Krister on Unsplash.